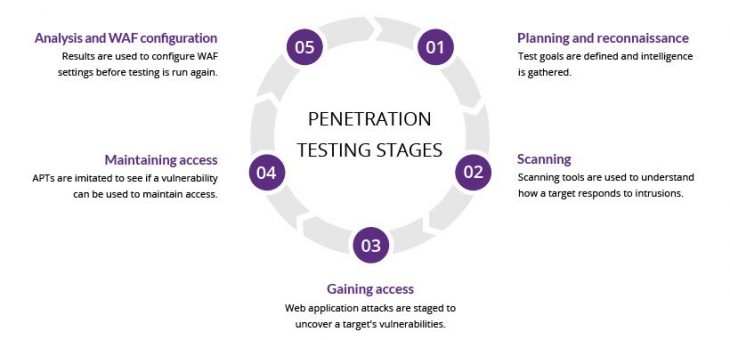
Penetration Testing & Vulnerability Scanning (Comparisons)
Is Penetration Testing and Vulnerability Scans The Same Thing? In the IT Security industry, technicians are prone to throwing around the phrases; Vulnerability Scans and Penetration Testing or Pen Test, and not realizing we might be confusing the public. So much so, we’ve made it far easier for any CEO or business owner to misunderstand […]