Cyber-attacks are like parasites: they are not always visible, not always felt, but with plenty of potential to affect your operational efficiencies, service level agreements, and computing resources. All of those impacts bring potentially high costs. The first step to understanding and managing the cost of cyber-attacks is to do everything you can to understand the potential impact and build an effective incident response team so you can rein in these “parasites” and limit damage to your business.
- Remember that crisis management is different than routine management- processes and objectives may be different
- Understand the impact on various arms, draw the lines of what can be absorbed
- Know that such events go beyond the IT only. It isn’t an IT-related issue, and require multiple executives’ attention and collaboration

Calculating the Cost of Cyber-Attacks
Despite the prevalence of cyber-attacks, Radware’s research has revealed that the vast majority of the world’s security experts (73%) have not devised a formula for calculating the financial impact of the attacks they suffer. Rather, they rely on estimates. Unfortunately, those estimates tend to be significantly lower than the findings of those who calculate actual costs. Most security experts (54%) estimate the impact of each cyber- attack at less than $100,000; only 12% estimated the cost of an attack to be $1 million or more (see Figure 1).

Similarly, Radware has uncovered differences across business sectors. While educational institutions continue to underestimate attack costs, healthcare, government and technology organizations are well aware of the risks. Indeed, such organizations provide estimates that are five times higher than education respondents’ estimates. For healthcare and government, this better understanding of risk may be associated with the sensitive nature of the information under their care. Respondents from retailers provided an above-average estimate of $800,000 per attack. After all, retailers depend on optimal service availability to run their operations; once hit with an attack, losses are immediate. Surprisingly, financial services organizations provide a relatively moderate estimate of just $500,000 per attack.

Organizations that do calculate monetary consequences of attacks cite a number of factors that they take into account. For at least half, reputational damage and revenue  loss are factors. Other drivers include SLA fees, legal damage, compliance fees and processing of unwanted traffic. The average cost among businesses that calculate the impact of a cyber-attack is almost double the estimate of other businesses: $1.1 million versus $620,000.
loss are factors. Other drivers include SLA fees, legal damage, compliance fees and processing of unwanted traffic. The average cost among businesses that calculate the impact of a cyber-attack is almost double the estimate of other businesses: $1.1 million versus $620,000.
Planning a Cyber-Combat Strategy
Radware inquired how organizations respond to such incidents.
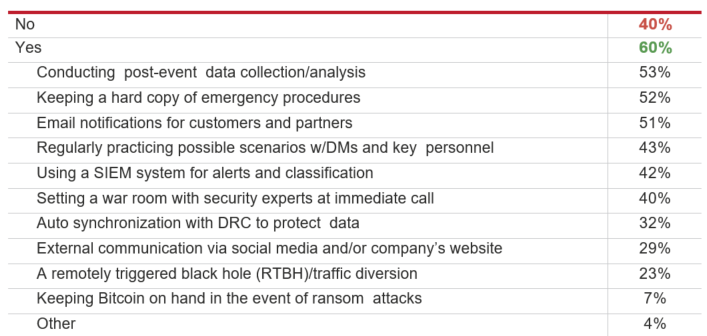
Forty percent of global respondents still lack a formal incident response plan.
That is a dangerous shortcoming. After all, cyber-attacks by definition disrupt “business as usual.” Of course, not all attacks are created equal. Some actually cause serious disruptions that pose a potential threat to the business—and must be handled immediately. How can you tell which attack you are dealing with?
You may be spending significantly on penetration testing and the latest technology for endpoint protection all the way down to BYOD mobile phones. Even so, you may be overlooking critical gaps. Think about everything. Use a bidirectional process where you draw your organization from the inside out, understanding your current information security architecture and looking for vulnerabilities. Consider who might want to hurt you, why and what means they may have to do so. These actors may include hacktivists, ransomers, competitors or even disgruntled insiders or customers.
Step 2 – Understand the Impact
Some costs can be easily added to the equation: What’s the cost of a minute of downtime? An hour? Are there any legal fees or compliance fines you would face if compromised? What would be the daily cost of investigating an attack (factor in-house labor as well as the costs of executives’ attention and technology partner services)?
Other financial impacts are harder to pin down – for example reputational impact, which can vary depending on the severity of the attack and how much time your organization spends in the headlines.
Step 3 – Prioritize Critical Missions
After estimating the different impacts, it becomes easier to determine what is essential for the organization to continue functioning. Prioritize business procedures and processes, engaging executive management for both their input as well as their endorsement and resource allocation. As much as possible, use key performance indicators to help measure the efficiency of the incident response plan.
Step 4 – Choose Your Squad
Once you have defined the critical processes, identify the dedicated personnel to run them. The incident response plan cannot be the sole purview of the cyber security team; other key players in the organization must also know how to orchestrate critical missions when enmeshed in a crisis. For the information security aspects of the breach, your team must include the best security experts in the organization. They should not only know how best to configure the product, but also know how to think like a hacker.
The “textbook” incident response team has system administrators who are very familiar with IT resources and how to back up data; network administrators who know network protocols and can dynamically reroute traffic; and information security personnel who know how to thoroughly track and trace security issues as well as perform post-mortem analysis of compromised systems.
Step 5 – Test, Revise, Adapt
An incident response plan is never “complete.” After all, the threat landscape is dynamic. So is every business and its network, information and collection of vendors it relies on to support operations. When a crisis occurs, there is no room for error; your response must be rapid and decisive. To meet that high standard, routinely stage “emergencies” and practice responding to them. In doing so, your organization will develop a methodology that fosters speed and accuracy while minimizing the impact of unavailable resources and potential damage should an actual crisis occur. These simulations should involve not only the cyber-security response team but also those responsible for the communications plan, along with your technology partners, service providers and relevant executive leaders.
In security, it is generally wise to invest in prevention over detection. With cyber-attacks likely to impact every business in some capacity, preparation is a major step toward mitigating successfully and minimizing the financial, reputational and legal havoc an attack can wreak.

Download “Web Application Security in a Digitally Connected World” to learn more.

Ben Zilberman
Ben Zilberman is a product marketing manager in Radware’s security team. In this role, Ben works closely with Radware’s Emergency Response Team to raise awareness of high profile and impending attacks. Ben has a diverse experience in network security, including firewalls, threat prevention, web security and DDoS technologies. Prior to joining Radware, Ben served as a trusted advisor to Checkpoint Software technologies where he led partnerships, collaborations, and campaigns with system integrators, service, and cloud providers and implemented best practices of security design and management. He also serves as a commercial instructor and public speaker. He holds a BA in Economics and a MBA, from Tel Aviv University.
