TRUST is mainly based on the outcome of security assessment. We will focus to report critical and high risk findings for all application functionalities.
Based in Singapore, MK Cybersecurity has experienced security researchers, best-in-class vulnerability scanners, security certifications and best-practice methodologies. If no critical or high risk finding is found, certifications, methodologies and vulnerability scanners are just decorations. Therefore, our best commitment to you is security reports with critical and high risk findings.
1. Singapore-based company
Based in Singapore, to assure you our best commitment and assessment quality, we are keen to report critical and high risk findings for all of your application functionalities.
The reports will comprise of executive summary, detail findings and recommended remediation for discovered vulnerabilities.
A level of trust will be established based on the assessment outcome.
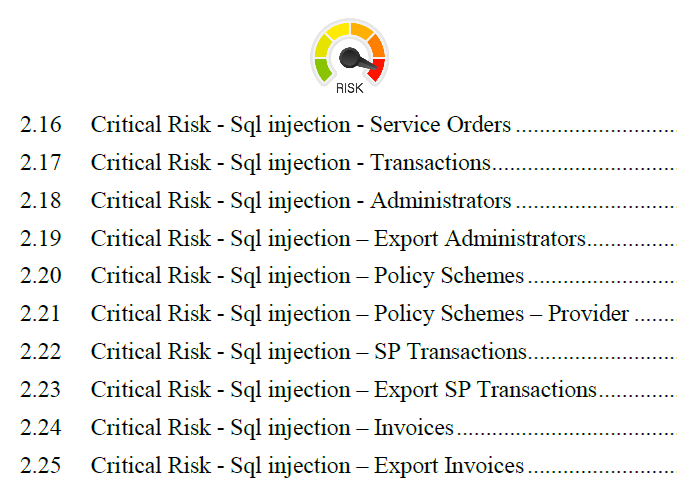
2. Assessment of ALL application functionalities
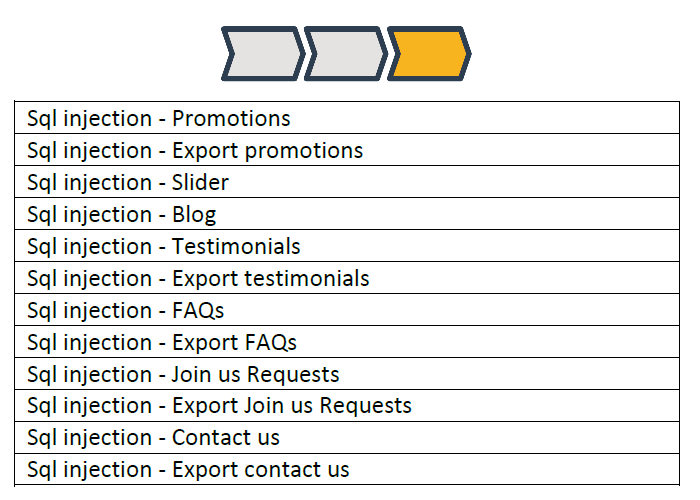
In penetration testing, our security researchers will examine all application functionalities for complex, application-context and cross-functional vulnerabilities.
Sample cross-functional vulnerabilities:
- Account takeover
- Server takeover
- Customer data leaking
- Database extraction
- Fake orders
- Fake payment
- Illegal balance manipulation
- …
Security researchers wil perform hacking techniques in controlled manner to form a comprehensive list of security vulnerabilities.
3. Trusted vulnerability scanners
Trusted vulnerability scanners Acunetix, Rapid7 and Nessus are used for vulnerability assessment. These scanners will reveal simple and common vulnerabilities in your websites, mobile application and servers.
In penetration testing, these vulnerability scanners are used as part of assessment. Security researchers will perform more manual hacking techniques for more complex and application-context vulnerabilities.

